Configure SSO with Okta
Set up single sign-on (SSO) logins with Okta as your identity provider.
About SSO with Okta
Shipium supports single sign-on (SSO) using Okta as your SAML identity provider. This document provides guidance for configuring SSO with Okta in the Shipium system. For more general information about SSO requirements and Shipium, see SSO for Your Shipium Account.
Configure SSO for your Shipium account using Okta as the identity provider
Step 1. Obtain values from Shipium
To start the process, Shipium's IT team will provide your team with an entity ID value and sign-in URL.
Step 2. Set up an Okta developer account
Your Shipium team member is available to assist as you set up Okta as your SAML identity provider, but the process is outlined in the following steps.
To begin, you'll need to sign up for an Okta developer account, which requires you to log in to your Okta account.
Step 3. Configure Okta SAML integration
Once you have a developer account with Okta and you sign in to the Okta Developer Console, you'll use the App Integration Wizard to add Shipium as an application for use. From the Okta navigation menu, you'll select Applications from the primary Applications menu.
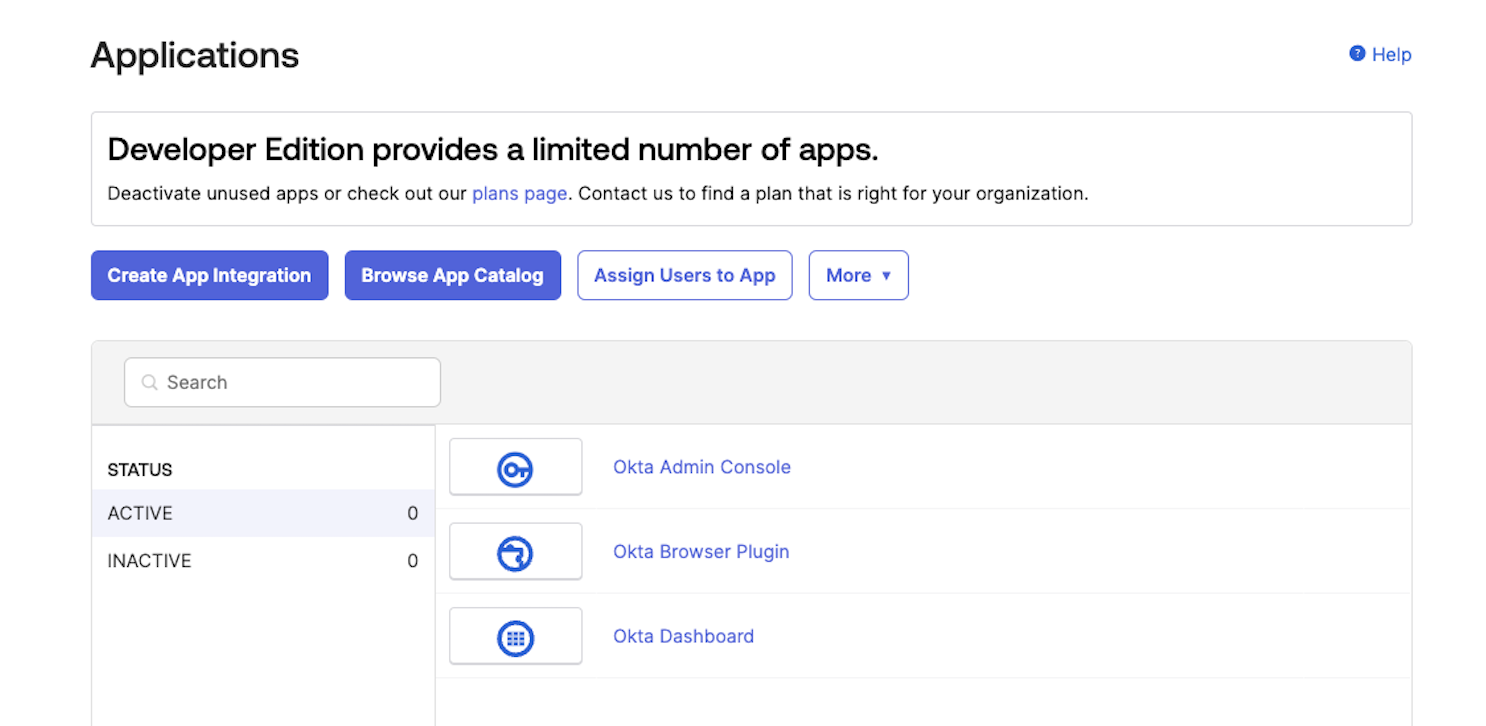
When prompted to select the sign-in method for the new app integration, you'll select SAML 2.0.
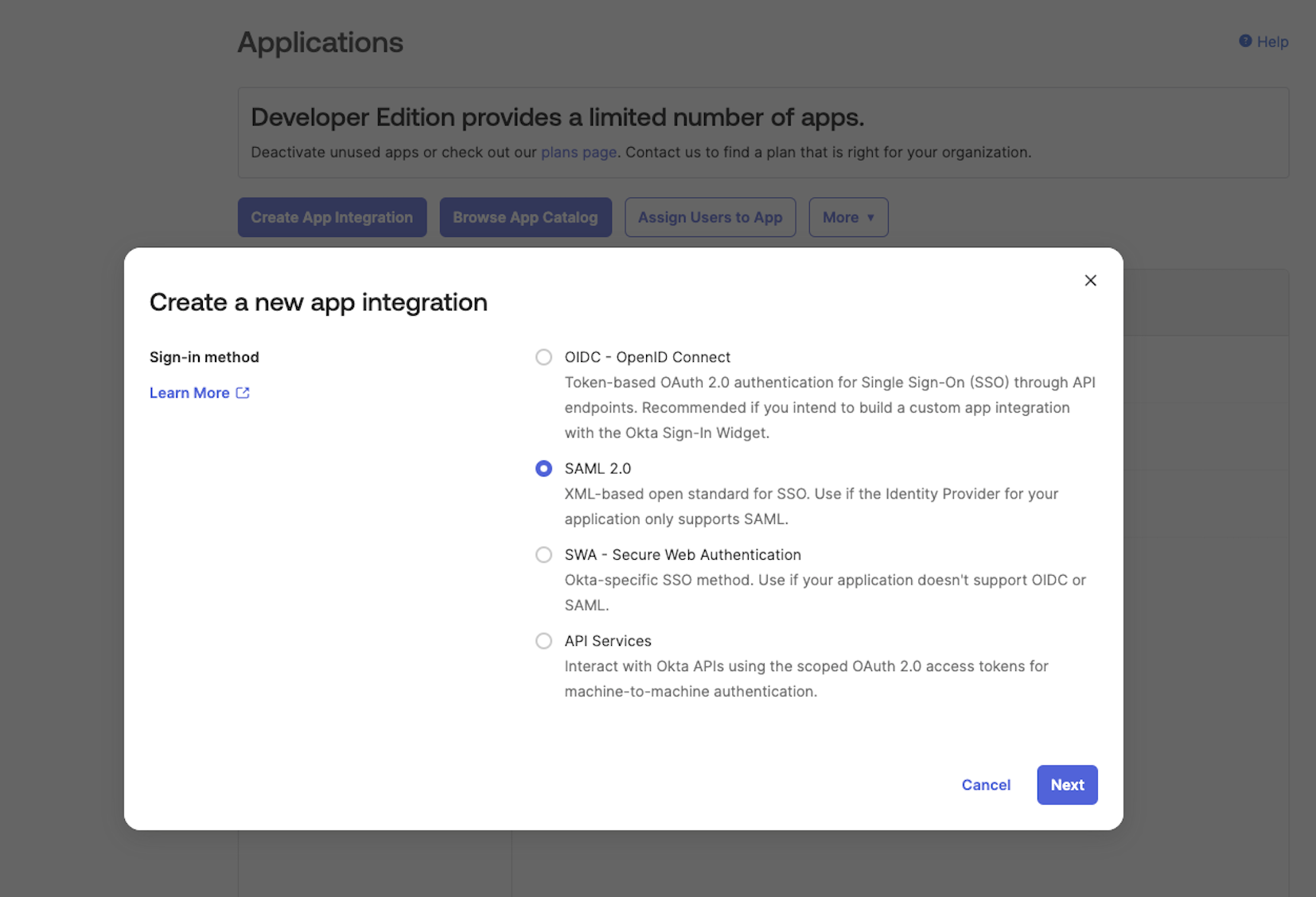
You'll use the SAML App Wizard within Okta to create the SAML integration. We suggest using Shipium as the app name.
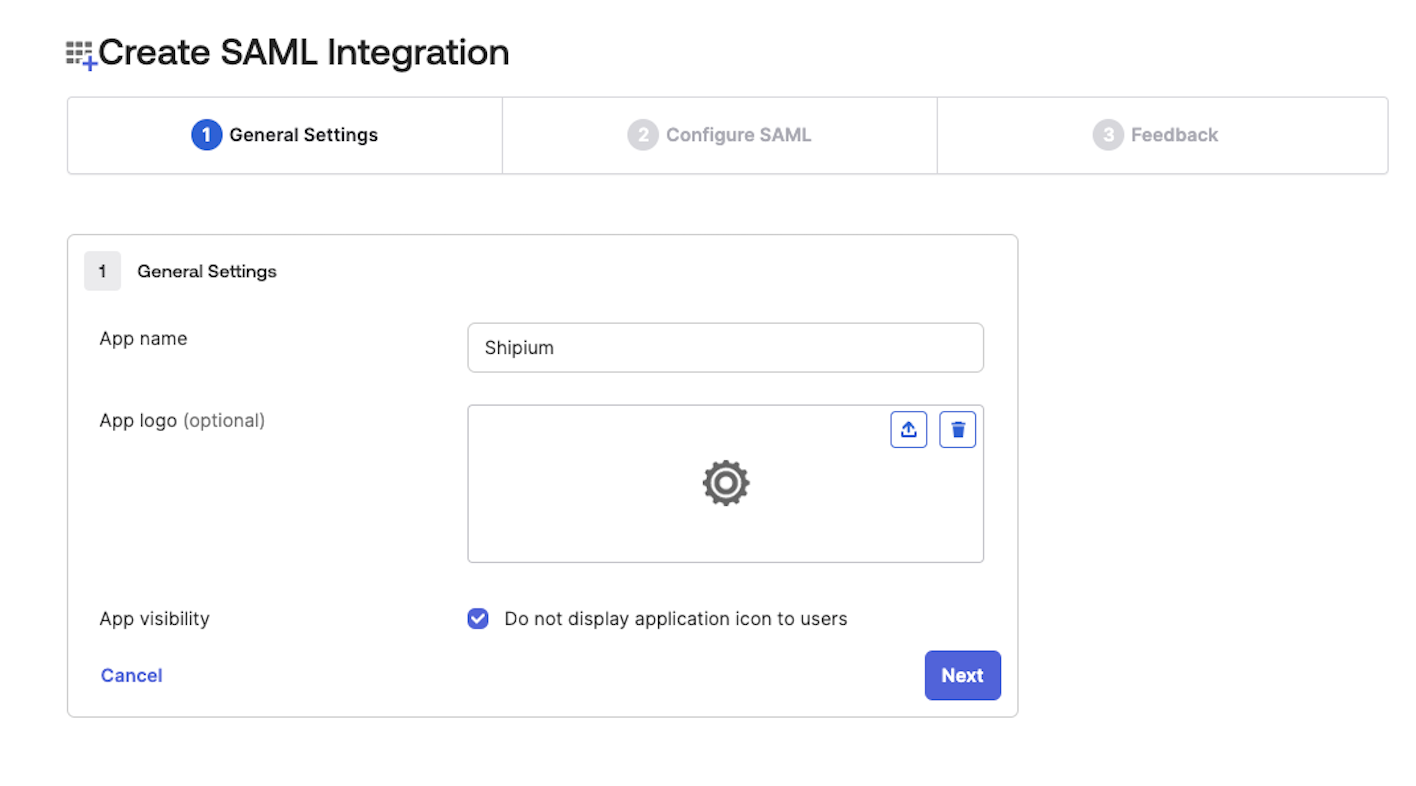
Next, you'll establish general and SAML settings for the Shipium app. A Shipium IT team member will provide the values you need for Single Sign-On URL and Audience URI (SP Entity ID). For Name ID Format, you'll select "Unspecified". From the next dropdown menus, you'll select "Email" for Application Username and "Create and update" for Update Application Username On.
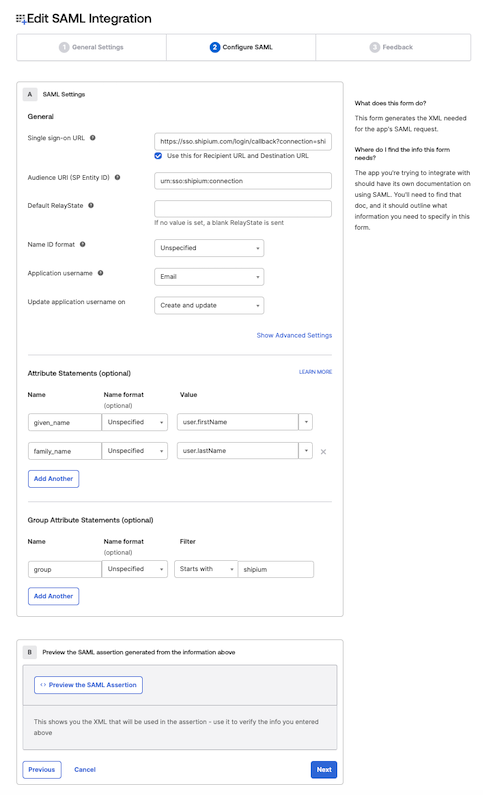
For the Attribute Statements (optional) section, you'll provide the values in the following table to determine the name structure for your account users.
| Name | Name format | Value |
|---|---|---|
| given_name | Unspecified | user.firstName |
| family_name | Unspecified | user.lastName |
The Group Attribute Statements (optional) section is optional for Shipium setup. This step enables group mapping, eliminating the need for user configuration in the Shipium Console following integration. If you choose to complete group provisioning at this step, you'll provide "group" as the Name, "Unspecified" as the Name Format, "Starts with" as the Filter, and "shipium" for the Filter field. You will also need to set up groups in Okta for the mapping to function correctly for users in your organization to have the following permission levels in the console:
shipium_admins, for users with administrator-level permissionsshipium_editors, for users with editor-level permissionsshipium_viewers, for users with viewer-level permissions
When you've completed this step, you'll click the Next button at the bottom of the screen. Once you select Next, Okta will request configuration information about your app integration. After making your selection, you will click Finish.
Step 4. View setup instructions for needed requirements
After completing the SAML integration with the app wizard, you'll be directed to the sign-on page for the newly created Shipium app. You'll click View SAML Setup Instructions to complete the process, but you'll want to note the identity provider single sign-on URL and download a copy of the X.509 certificate before proceeding.
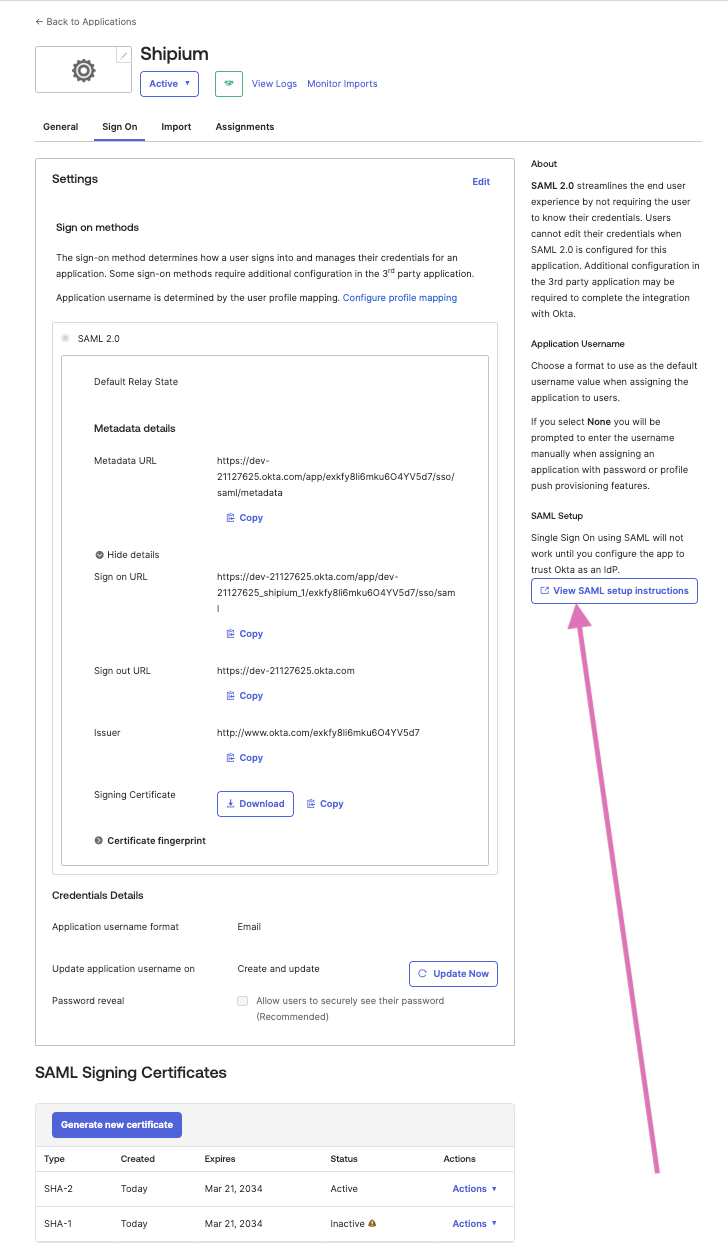
The SAML setup instructions will provide the information Shipium needs to complete setup on our end. You can simply copy the Identity Provider (IdP) Metadata XML file from the Optional section and provide that value to Shipium. Alternatively, you can share the Identity Provider Single Sign-On URL, Indentity Provider Issuer, and X.509 Certificate values with your Shipium team member.
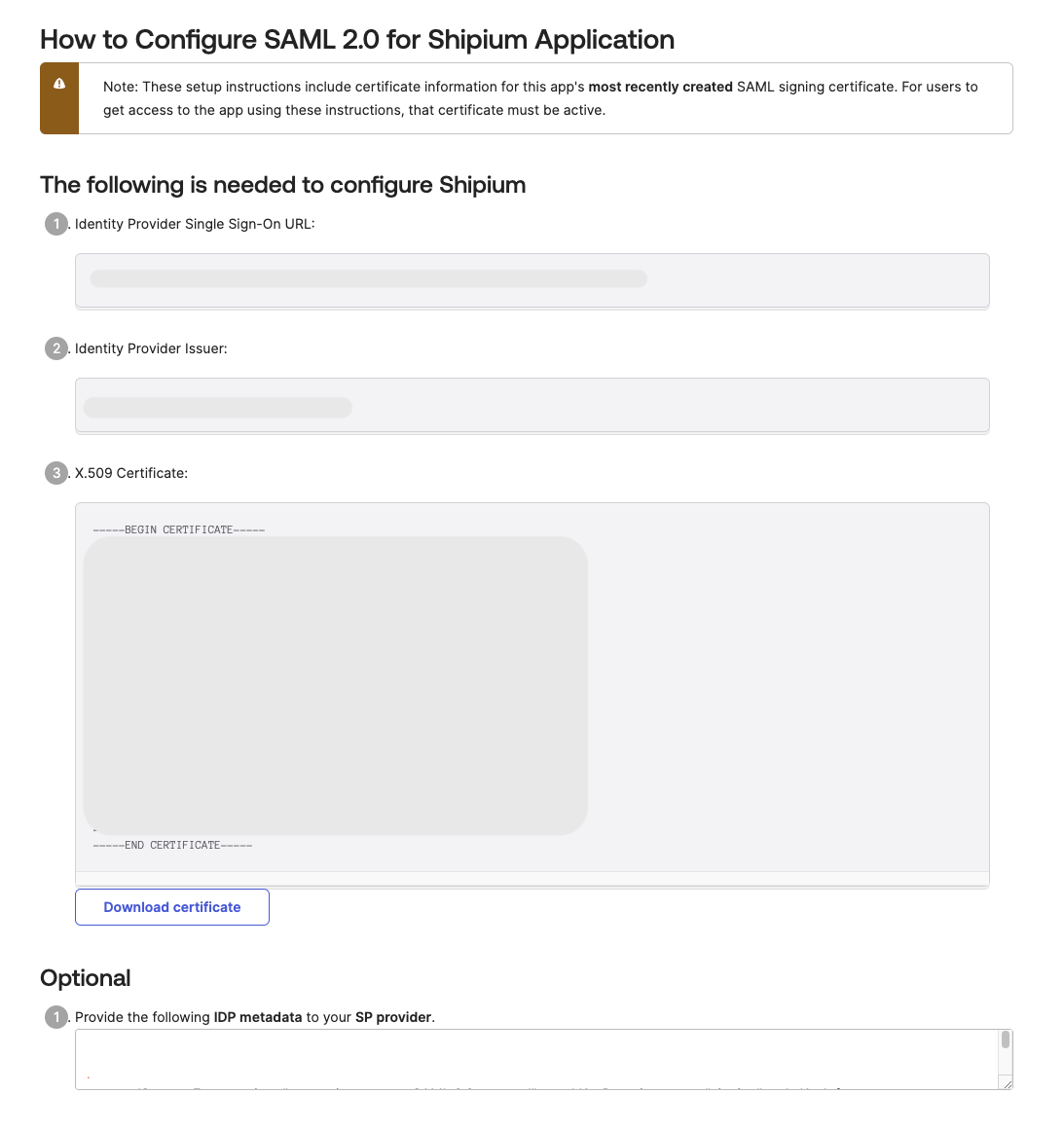
Step 5. Provide credentials to Shipium
To configure SSO for your organization's account users, you'll need to provide the following values to Shipium's IT team:
- Sign-in URL
- Sign-out URL
- X.509 signing certificate
- Email address attribute (optional)
You can find details about these requirements in Requirements for Configuring SSO with Shipium.
Resources
Your Shipium team member is available to help along the way. However, you might find these resources helpful:
Updated 4 months ago
